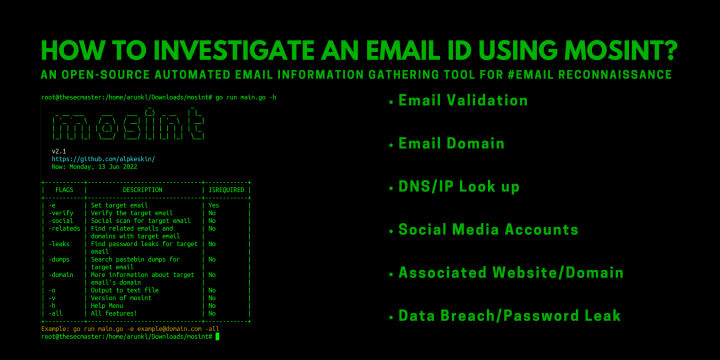
Step-by-Step Procedure to Join Ubuntu to an Active Directory Certificate Authority
Are you an IT professional considering joining Ubuntu to an Active Directory (AD) domain? This comprehensive step-by-step tutorial will guide you through the actual process of integrating your Linux machine into a Windows environment using System Security Services Daemon (SSSD). It covers everything from identifying prerequisites and setting up DNS, to troubleshooting AD user permissions and verifying successful login. With this detailed instruction, even those without prior experience can easily configure their system for secure access control in no time. A Short Note About SSSD & Realmd System Security Services Daemon (SSSD) is an open-source service developed to allow Unix and Linux machines to authenticate via localized user accounts as easily and quickly as possible, while also allowing secure communication across the network between the client machine and Active Directory. SSSD works…