What is New in KB5030219- September Cumulative Update for Windows 11?
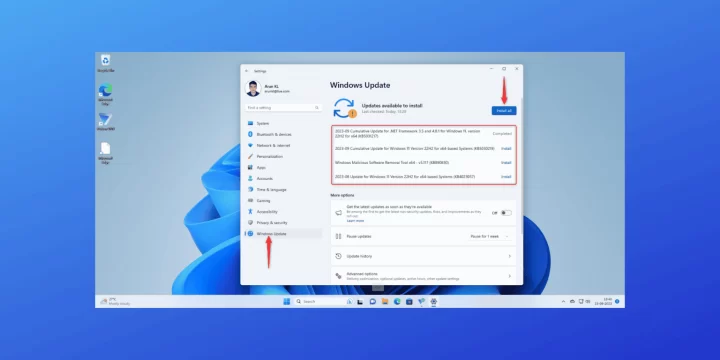
Microsoft recently rolled out the KB5030219 cumulative update for Windows 11 on September 12, 2023. This update is part of the monthly Patch Tuesday updates and includes security fixes as well as improvements and fixes for issues in Windows 11. Microsoft made this cumulative update- KB5030219 available for both Windows 11 versions 22H2 and 21H2. It can be installed on devices running Windows 11 Home, Pro, Pro for Workstations, Enterprise, and Education editions. Microsoft announced 24 months of support for Home, Pro, Pro for Workstations, and Pro Education editions and 36 months of support for its Enterprise and Education editions. This mandatory update contains security fixes for 24 vulnerabilities in Windows 11. Additionally, it also includes quality improvements for the servicing stack, the component responsible for installing Windows updates. In…