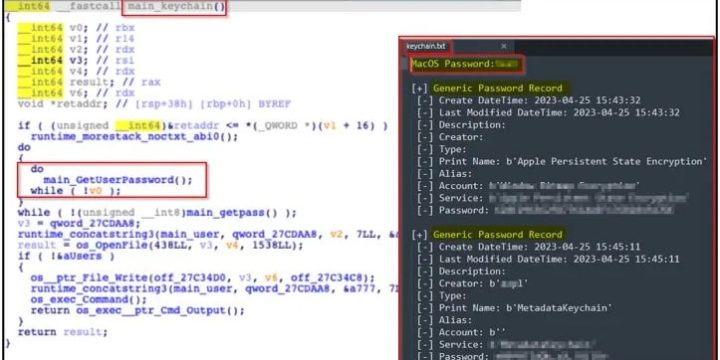
A New Security Evasion Technique- MalDoc in PDF
Cybercriminals are always looking for new ways to evade security systems and deliver malware. To stay one step ahead, security researchers actively look for and disclose new attack techniques to raise awareness. Recently, researchers from JPCERT/CC discovered a new polyglot security evasion technique that uses PDF files to bypass malware detection and deliver infected Word documents containing malicious macros. JPCERT named this technique “MalDoc in PDF”. In this blog post, we tried explaining the workings of the MalDoc in PDF attack and ways security engineers can upgrade their defenses against this ingenious new technique. Let’s get started! What is a Polyglot File? A polyglot file is a file that is valid in multiple file formats. This allows the file to exhibit different behaviors when interpreted by different programs. For example, a file…