Google has fixed these vulnerabilities by rolling out an update on the 16th of August. The company also said that the CVE-2022-2856 vulnerability is actively being exploited in the wild. The flaw is marked as a High severity vulnerability stemming from improper validation of untrusted input in Intents. Here is the tweet from Hossein Lotfi, a researcher from the Zero-Day-Initiative program from TrendMicro. Hossein Lotfi said in his tweet, “If an intent contains any extras or a data URI and it targets another browser, Google Chrome would open that browser with that URL without prompting.”
Google Chrome (In-The-Wild) Zero day (CVE-2022-2856) fix. If an intent contains any extras or a data URI and it targets another browser, Google Chrome would open that browser with that URL without prompting:https://t.co/iiDhLShhJv— Hossein Lotfi (@hosselot) August 18, 2022
What Are Web Intents?
Web Intents is a new technology that allows web applications to interact with each other without having to be explicitly developed for those interactions. For example, an app that provides sharing functionality can register a “share” intent, which would allow any other app that also provides sharing functionality to handle that request. This makes it easy for users to share content from one app to another without having to worry about which apps support which sharing methods.
Overall, Web Intents provides a way for web apps to interact with each other in a more natural and user-friendly way, as well as making it easier for developers to add new features to their apps.
10 New 0-Day Vulnerabilities in Chrome:
In the update Google shared, it has fixed these 10 0-day vulnerabilities in Chrome, of which 1 is Critical, 6 High, and 3 are Medium in severity.
- CVE-2022-2852: It’s a Critical severity vulnerability in FedCM.
- CVE-2022-2854: It’s a High severity vulnerability in SwiftShader.
- CVE-2022-2855: It’s a High severity vulnerability in ANGLE.
- CVE-2022-2857: It’s a High severity vulnerability in Blink.
- CVE-2022-2858: It’s a High severity vulnerability in Sign-In Flow.
- CVE-2022-2853: It’s a High severity Heap buffer overflow vulnerability in Downloads.
- CVE-2022-2856: It’s a High severity vulnerability due to insufficient validation of untrusted input in Intents.
- CVE-2022-2859: It’s a Medium severity vulnerability in Chrome OS Shell.
- CVE-2022-2860: It’s a Medium severity vulnerability due to insufficient policy enforcement in Cookies.
- CVE-2022-2861: It’s a Medium severity vulnerability due to inappropriate implementation in Extensions API.
Google’s Recommendation to Fix 10 New 0-Day Vulnerabilities in Chrome:
The Stable channel from Google has rolled out patches with the new release. Mac and Linux users should update Chrome to v104.0.5112.101, and corresponding Windows users should update their Chrome to v104.0.5112.102/101 to fix the vulnerabilities.
How to Update Chrome Browser?
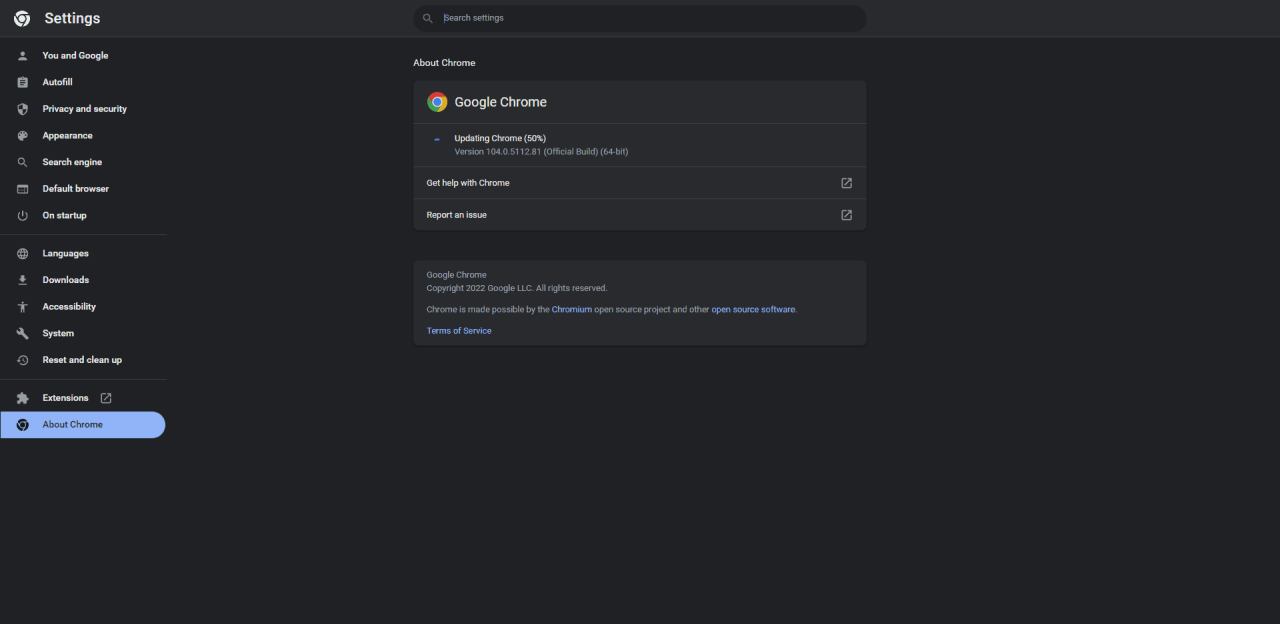
The update procedure is very simple. It’s just a matter of a couple of clicks.
Time needed: 5 minutes.
How to Update Chrome Browser?
See Also What Is Arbitrary File Upload Vulnerability? How To Protect Form It?
- Open ‘About Google Chrome’ on the browserLocket the three dots buttons at the top right corner of the window. A drop down will appear.
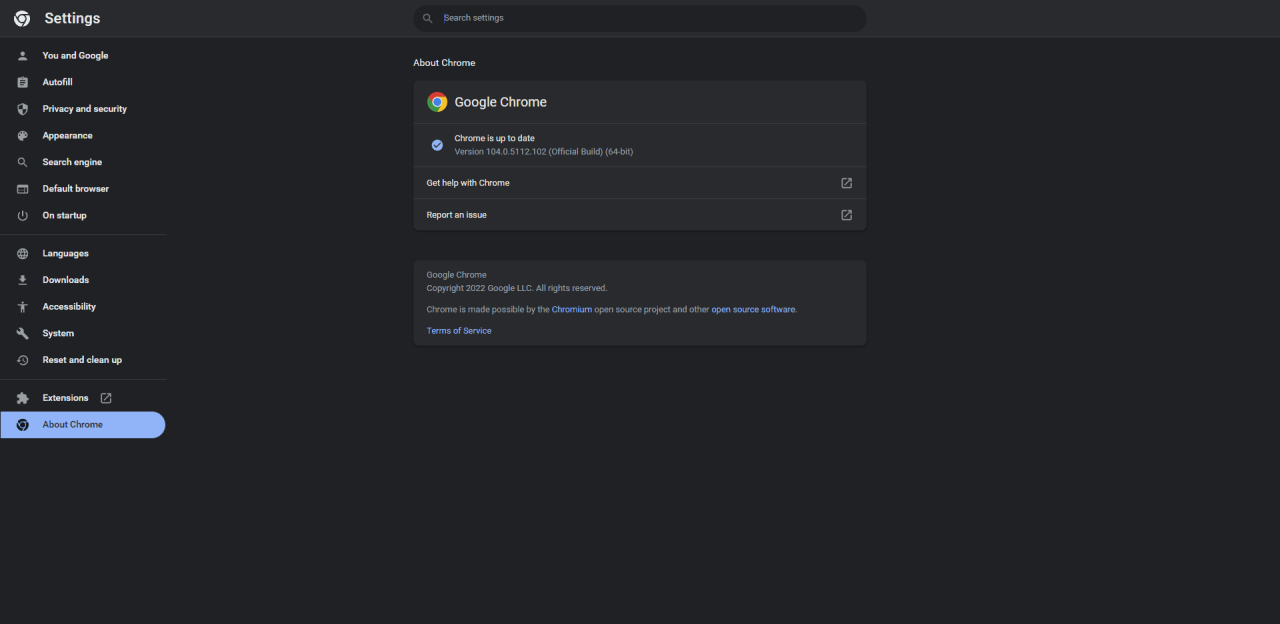
Then select Help > About Google Chrome from the drop down. Update will start by itself if your machine is connected to the internet. In this example, we have a Chrome running v104.0.5112.081. The Chrome has started the update process by itself.- Relaunch the Browser to complete the updateAfter the update gets completed, a ‘Relaunch’ button will appear. Click on it to relaunch the browser to complete the update process.